Some things just make life feel more complete. A quiet moment with your favorite hobby. A puzzle that wakes up your brain. Watching a plant grow on your windowsill. Or simply knowing your loved ones got home safe. These aren’t big, dramatic moments — they are the small, steady rhythms that keep us grounded.
In the middle of a busy day, having a little help with the things that matter most can make all the difference. Not just to save time, but to feel more connected — to what we love, what we are curious about, and who we care for.
From collecting coins to caring for plants, keeping your mind sharp or your family close — there are now tools designed to support what you already enjoy. Smart, simple, and genuinely useful, the right apps can quietly improve your daily routine in surprising ways. So, meet and explore four that do exactly that.
Coin ID Scanner: Unlock the Story Behind Every Coin
Every coin has a story — sometimes it’s just spare change, but other times, it is a hidden piece of history. And the good news is that you can be just a seasoned collector, a curious beginner, or someone who stumbled upon an old coin in a drawer, there is something incredibly satisfying about discovering where it came from and what it might be worth.
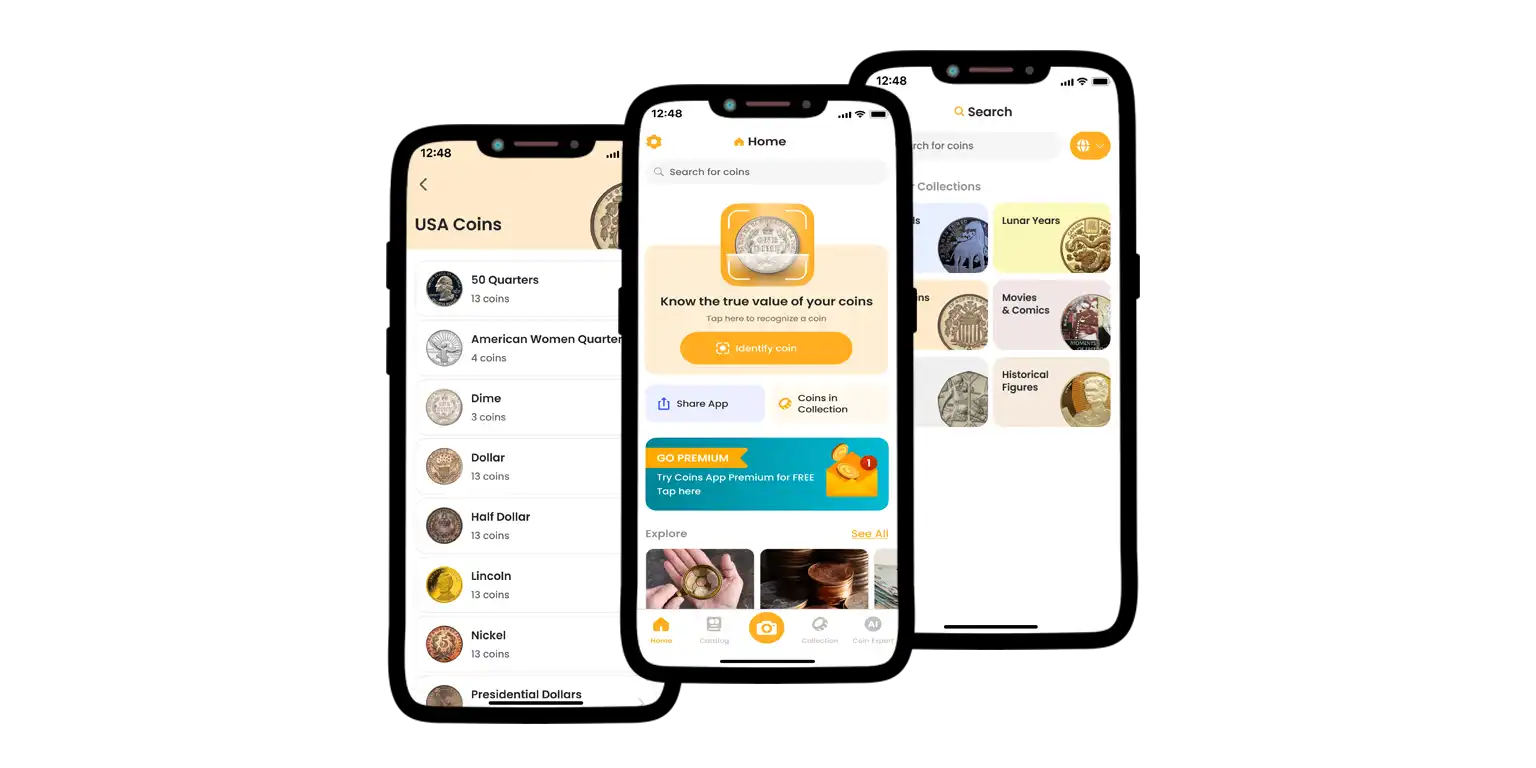
That is where Coin ID Scanner comes in. This smart coin scanner turns your phone into a personal numismatist in seconds. Just snap a photo, and easily identify the coin, estimate its value, and receive detailed data about its origin and condition.
What makes it special and useful?
- Instantly scans both sides of any coin
- Works with coins from around the world, including ancient and foreign
- Provides historical background, rarity info and market price estimates
- Offers tips on grading, preservation, and selling or even experts’ insights in the blog
So, whether you are cataloging a personal collection or just exploring a new hobby, Coin ID Scanner makes the experience easy, educational, and even a little addictive. It’s more than just identifying metal — it’s about connecting with stories, places, and eras you may have never noticed before.
Mind Elevate: Small Games, Big Mental Shifts
Mental clarity doesn’t have to come from silence, meditation, or hours of effort. Sometimes, all it takes is five minutes of the right kind of play. Mind Elevate app is built on that idea — it is not just another brain training app, but a daily ritual disguised as fun.
Packed with fun brain games, the app sharpens focus, boosts memory, and encourages quicker thinking through short, addictive exercises that actually challenge your mind — not bore it. It feels like a game, but it leaves your brain feeling recharged, not drained.
Here’s what makes Mind Elevate different:
- Games adapt to your skill level and get smarter as you do
- Visuals are clean, playful, and never overwhelming
- Sessions are short — perfect for a coffee break or commute
- Tracks your progress in memory, logic, focus, and speed
The app is a good tool for people who like mental challenges but don’t have time (or patience) for complex systems. If you are trying to stay sharp for work, studying, or just enjoy a mental refresh after a long day, Mind Elevate makes it easy to make brain health part of your everyday rhythm — and actually look forward to it.

Plant Finder: Bring Nature Closer — and Smarter
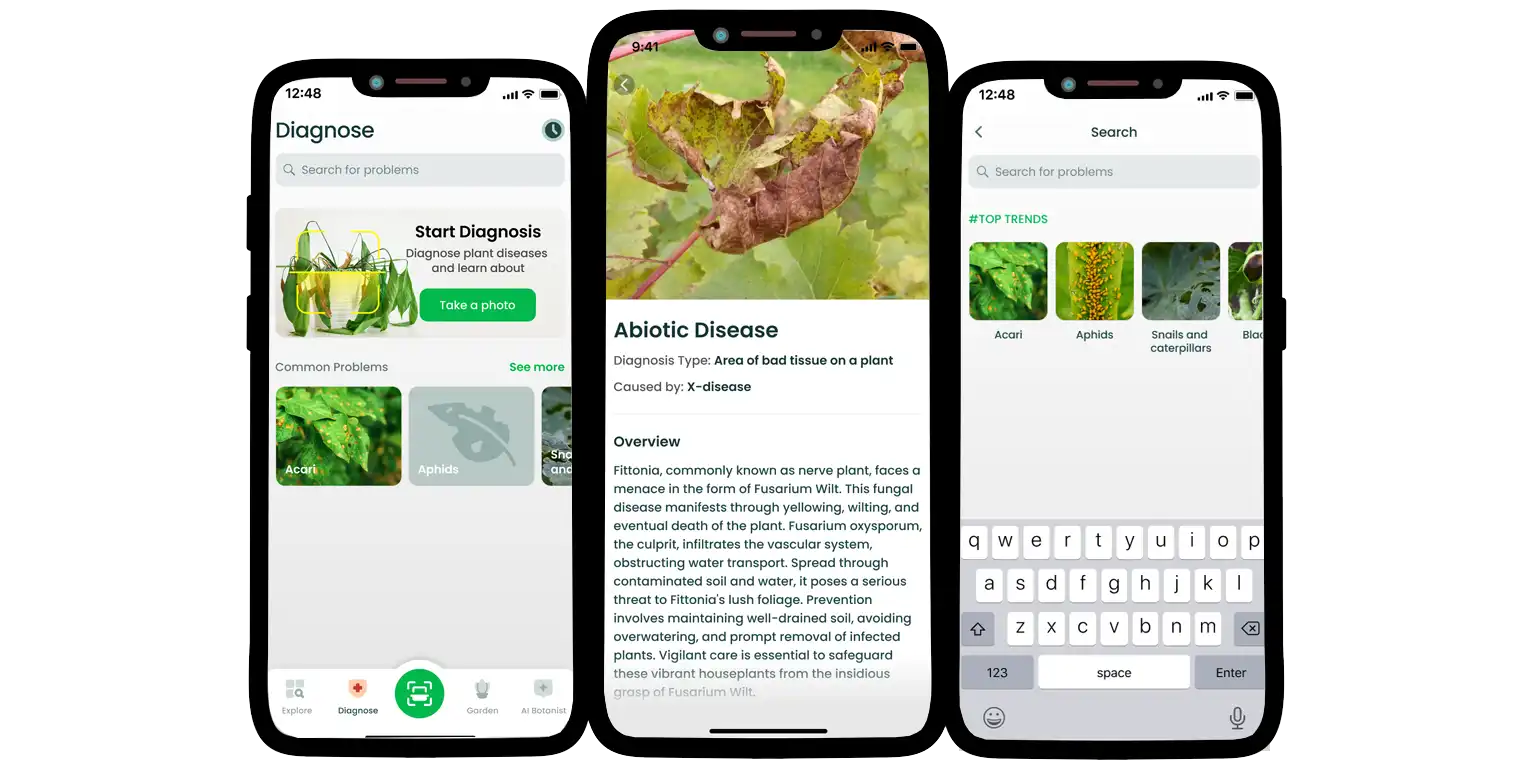
There is something calming about being around plants — but that calm quickly disappears when you realize you have no idea what’s growing on your balcony or why your fern suddenly turned brown. That is where Plant Finder steps in. This intelligent AI plant identifier helps turn guesswork into confidence, whether you are a plant newbie or a full-on botanical lover.
Just snap a photo, and the app identifies the plant species instantly. But it doesn’t stop there — it offers rich, practical advice that makes caring for your plants less about trial and error and more about real understanding.
Here’s what Plant Finder can do:
- Instantly recognize thousands of plant species and varieties
- Offer tailored care tips based on plant type and condition
- Diagnose common plant problems and suggest solutions
- Offers watering or maintenance reminders that you can customize for each of your green favorites
Perfect for indoor gardeners, weekend balcony growers, or curious hikers who want to identify what they see along the trail, Plant Finder turns your phone into a pocket-sized botanist. And be sure the app is not just about knowing the name — but more about forming a better relationship with the living things around you.
Number Tracker: Peace of Mind in Your Pocket
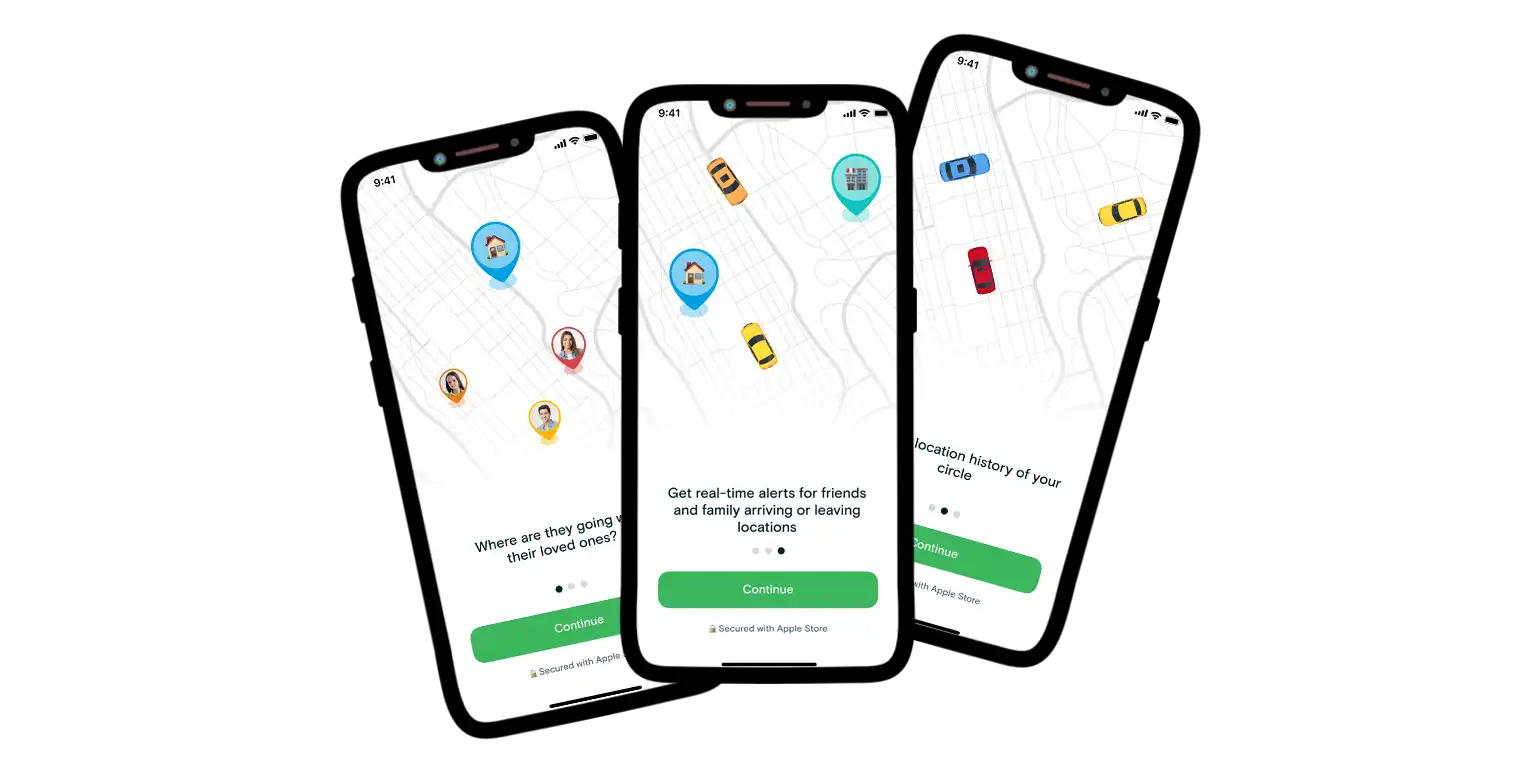
Keeping track of the people you care about shouldn’t feel like surveillance — it should feel like peace of mind. We know, you are often wondering how to track my child’s phone on their walk home or just want to know your partner landed safely, so your solution is the Number Tracker app. With it you finally got a gentle but powerful way to stay connected.
The app is a good idea for all: families, friends and anyone who wants an extra layer of security. This smart location-sharing app offers real-time updates without being invasive.
Why you will love using Number Tracker:
- Real-time location tracking with detailed route history
- Custom safety places — get alerts when someone enters or leaves a set place like home, school or gym.
- Low battery and very precise to stay informed in emergencies
- Clean, intuitive interface anyone can use, no tech skills required
Ideal for parents, caregivers, couples in long-distance relationships, or even close-knit friend groups, Number Tracker turns your smartphone into a quiet safety net. It answers questions before you even have to ask — and lets everyone breathe a little easier, knowing they’re never truly out of reach.
Simple Apps, Big Impact
Everyday life is full of moments that matter — quiet curiosities, small challenges, and the people and things we care about most. The right tools don’t complicate these moments, they enrich them. All of the apps above can prove that superpowers don’t have to be flashy or complicated — sometimes, they’re just smart, simple helpers that make your day a little easier and a lot more meaningful. With these four apps, everyday routines turn into chances to connect, grow, and feel safe. Your digital superpowers are ready. It’s time to install and unlock them.

